- cross-posted to:
- privacy@lemmy.world
- cross-posted to:
- privacy@lemmy.world
“Temu is designed to make this expansive access undetected, even by sophisticated users,” Griffin’s complaint said. “Once installed, Temu can recompile itself and change properties, including overriding the data privacy settings users believe they have in place.”
That’s just nuts
Yeah, it is. It’s such an extraordinary claim.
One requiring extraordinary evidence that wasn’t provided.
“It’s doing amazing hacks to access everything and it’s so good at it it’s undetectable!” Right, how convenient.
Libmanwe-lib.so is a library file in machine language (compiled). A Google search reveals that it is exclusively mentioned in the context of PDD software—all five search results refer to PDD’s apps. According to this discussion on GitHub, “the malicious code of PDD is protected by two sets of VMPs (manwe, nvwa)”. Libmanwe is the library to use manwe.
An anonymous user uploaded a decompiled version of libmanwe-lib to GitHub. It reads like it is a list of methods to encrypt, decrypt or shift integer signals, which fits the above description as a VMP for the sake of hiding a program’s purpose.
In plain words, TEMU’s app employed a PDD proprietary measure to hide malicious code in an opaque bubble within the application’s executables
So wait, bit-shifting some integers is now considered being malicious? Is that really the defense here? Using that definition just about all software in existence is malicious.
deleted by creator
deleted by creator
I don’t believe his claims without evidence, but having a legit cover for nefarious acts is pretty standard, no?
deleted by creator
Why steal their money when they can both get them to give their money as well data to also sell?
This is why companies like Apple are at least a tiny bit correct when they go on about app security and limiting code execution. The fact it aligns with their creed of controlling all of the technology they sell makes the whole debate a mess, though. And it does not excuse shitty behavior on their part.
But damn
And if they got this past Apple in their platforms. That’s even wilder.
The article linked to the analysis and on a quick glance, it seems to be done entirely against the Android variant of the app. This makes sense because if the alleged actions are true, they’d never have gotten on to the App Store for iOS Apple users… or at least as of a couple months ago. Who knows what kind of vulnerability is exposed by Apple only doing limited cursory checks for 3rd party App Stores.
Shits getting scarier by the day.
deleted by creator
- Dynamic compilation using runtime.exec(). A cryptically named function in the source code calls for “package compile”, using runtime.exec(). This means a new program is created by the app itself.—Compiling is the process of creating a computer executable from a human-readable code. The executable created by this function is not visible to security scans before or during installation of the app, or even with elaborate penetration testing. Therefore, TEMU’s app could have passed all the tests for approval into Google’s Play Store, despite having an open door built in for an unbounded use of exploitative methods. The local compilation even allows the software to make use of other data on the device that itself could have been created dynamically and with information from TEMU’s servers.
Ah yes, delete your original incorrect comment instead of continuing the discussion about how wrong and lazy it was to make, nice.
I’m sure Temu collects all information you put into the app and your behaviour in it, but this guy is making some very bold claims about things that just aren’t possible unless Temu is packing some serious 0-days.
For example he says the app is collecting your fingerprint data. How would that even happen? Apps don’t have access to fingerprint data, because the operating system just reports to the app “a valid fingerprint was scanned” or “an unknown fingerprint was scanned”, and the actual fingerprint never goes anywhere. Is Temu doing an undetected root/jailbreak, then installing custom drivers for the fingerprint sensor to change how it works?
And this is just one claim. It’s just full of bullshit. To do everything listed there it would have to do multiple major exploits that are on state-actor level and wouldn’t be wasted on such trivial purpose. Because now that’s it’s “revealed”, Google and Apple would patch them immediately.
But there is nothing to patch, because most of the claims here are just bullshit, with no technical proof whatsoever.
The study and evidence was already provided months ago
This was also linked in the article if you read it
Here’s the actual relevant part

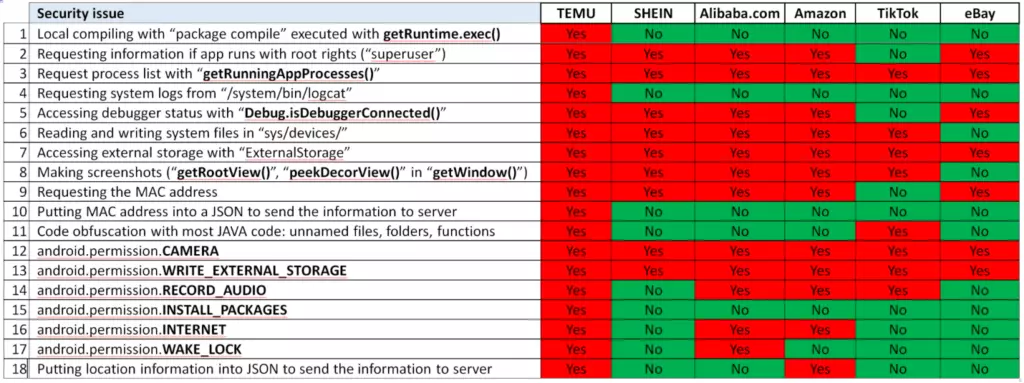
These are security risks to be sure, and while these permissions are (mostly) on the surface, possibly defensible, together they do clearly represent an app trying to gather all of the data that it can.
However, a lot of info from this report is overblown. For example code compilation is sketchy to be sure, but without a privilege escalation attack, it can’t do anything the app couldn’t do with an update.
Also, there’s some weird language in the report, like counting the green security issues in other apps (like tiktok) as if they were also a problem, despite the image showing that green here means it doesn’t present that particular risk.
All of this to say, if you have temu, probably uninstall it. It’s clearly collecting all the data it can get.
But it’s unlikely to be the immediate threat that will have China taking over your phone like this report implies.
This infographic is really helpful. Stuff like this makes me relieved I use the majority of services in a browser, rather than native apps
I’m blown away by how many people use apps when they don’t have to. There’s a reason companies are always trying to get you to download their app, and it’s so they can put their software on your phone and harvest more of your data.
Exactly why I use browser and not apps, too. and if they try to strongarm me with better prices or degraded services, I just stop using them all together.
It’s why I stopped using Reddit on mobile lol. No, I don’t want to download your official app, and no you making it so I need it to access NSFW stuff will convince me to.
Same with X/Twitter. I hate when people put information in those now because you can’t read more than one at a time in some reply to self thread on there without downloading the app. Especially when it’s important news or on the ground reporting. Screw that. All those reporters need to use mastadon.
Yup. I used to watch TikTok’s sent to me. Now I can’t. They want me to use their app. LOL. Nah.
Thanks, that brings done useful context here
That… is not a study by anyone who knows what they are talking about. It also does not mention fingerprints at all.
They seem to believe that the app can use permissions undeclared in the manifest file because they obviously think it’s only for the store to show the permissions to the user. Android will not actually allow an app to use undeclared permissions. The most rational explanation is the codebase is shared with different version of the app (possibly not released) that had different manifests.
It also makes a big deal of checking if running as root. That is not evidence of having an escalation exploit. If they have an ability to get root before running the app why would they need to use the app to exploit it? They could just do whatever they wanted and avoid leaving traces in the app. Though I doubt they would root phones to just brick them. It’s the kind of mischief you would expect from a kid writing viruses, not an intelligence agency or criminal enterprise.
Users who root their own phones are very unlikely to run temu as root. In fact a lot of apps related to shopping or banking try to detect root to refuse to work as your system is unsafely. In any case it’s a very niche group to target.
To keep things short, that ‘study’ does not really look credible or written by actual experts.
The article links to this as technical proof https://grizzlyreports.com/we-believe-pdd-is-a-dying-fraudulent-company-and-its-shopping-app-temu-is-cleverly-hidden-spyware-that-poses-an-urgent-security-threat-to-u-s-national-interests/
There’s analysis of decompiled source code.
The analysis shows it’s spyware, which I don’t question. But it’s spyware in the bounds of Android security, doesn’t hack anything, doesn’t have access to anything it shouldn’t, and uses normal Android permissions that you have to grant for it to have access to the data.
For example the article mentions it’s making screenshots, but doesn’t mention that it’s only screenshots of itself. It can never see your other apps or access any of your data outside of it that you didn’t give it permission to access.
Don’t get me wrong, it’s very bad and seems to siphon off any data it can get it’s hands on. But it doesn’t bypass any security, and many claims in the article are sensational and don’t appear in the Grizzly report.
I agree on the sensationalism in the article.
Still sounds like shitty company doing shitty things
That is not entirely correct. The reported found the app using permissions that are not covered by the manifest. It also found the app being capable to execute arbitrary code send by temu. So it cannot be clearly answered if the app can utilize these permissions or not. Obviously they would not ship such an exploit with the app directly.
The reported found the app using permissions that are not covered by the manifest.
It didn’t found them using them, it’s an important distinction. It found code referring to permissions that are not covered by the Manifest file. If that code was ran, the app would crash, because Android won’t let an app request and use a permission not in the Manifest file. The Manifest file is not an informational overview, it’s the mechanism through which apps can declare permissions that they want Android to allow them to request. If it’s not in the Manifest, then it’s not possible to use. It’s not unusual to have a bunch of libraries in an app that have functionality you don’t use, and so don’t declare the required permissions in the Manifest, because you don’t use them.
It also found the app being capable to execute arbitrary code send by temu.
Yeah, which is shady, but again, there is nothing to indicate that code can go around any security and do any of the sensational things the article claims.
The Grizzly reports shows how the app tricks you into granting permissions that it shouldn’t need, very shady stuff. But it also shows they don’t have a magical way of going around the permissions. The user has to actually grant them.
Do you know if there people who have gone this far analysing the TikTok and WeChat apps?
Yeah, I don’t like Temu, and I’m sure the app is a privacy nightmare, but these claims don’t seem right. If it’s true, I’d like to see someone else verify it.
Haven’t read the article because I’m not interested in an app I don’t use, but does it mean browser fingerprint? Because that’s slang for the fonts/cookies/user-data of your browser, and lots of apps have access to that.
Wouldn’t the phone have to have your fingerprint stored in order to compare it to the one scanned?
Yes, the phone does, but that data is protected in the hardware and never sent to the software, the hardware basically just sends ok / not ok. It’s not impossible to hack in theory, nothing is, but it would be a very major security exploit in itself that would deserve a bunch of articles on it’s own. And would likely be device specific vulnerability, not something an app just does wherever installed.
Pretty sure this is not true. That’s how apple’s fingerprint scanners work. On android the fingerprint data is stored either in the tpm or a part of the storage encrypted by it.
Yeah, so the app never sees it. What are you disagreeing with?
I just corrected that, can’t I without disagreeing?
I mean that I don’t know what part of my comment is “not true”. I welcome corrections, I just don’t see what is being corrected here.
It doesn’t send a yes/no signal it sends the fingerprint to be compared to the stored one
Temu is absolute cancer in terms of business practices so no surprise here at all.
Cancer in terms of, well, everything.
But it’s cheap.
Cheap cancer
If I wanted garbage I could get it for free from the roadside
Why is Temu so popular then?
Because people get dopamine from shopping, even if it’s garbage. It causes enormous amounts of waste, because most of the crap isn’t used much if at all. They just make it look good on the product page.
…and it’s cheap.
How about pass and enforce strong digital privacy protection laws you fucking cowards. When other countries spy on us it’s scary and bad, but for US companies? Best we can do is ban porn and demand backdoors to stop E2EE messaging.
California (and a few other states) are trying. The CCPA and CPRA are a good step in the right direction. If you’re a California resident, you can request all the data a business has collected about you, tell them to stop sharing it with business partners, or tell them to completely delete it, similar to the GDPR in Europe.
Oh don’t worry, they’re going to try and kill that too before it hurts them too much, and with the audacity of calling it the “American Privacy Rights Act”. https://www.eff.org/deeplinks/2024/06/eff-opposes-american-privacy-rights-act
Ugh. I hate this so much.
I’m pretty sure Temu is Chinese.
Unfortunately they care more about spying on us themselves.
That would hurt the advertising, spam, blackmail, malware, and propaganda industries. We can’t rip out the economic spine of big tech since they pay the best bribes.
I can’t believe anyone would buy from Temu. I knew they were Chinese knockoff bullshit the second I saw their first obnoxious ad.
Plenty of items on eBay are just people who buy from China directly and mark up prices. If it is likely made in China and I don’t want it quickly, I’ll buy off aliexpress. That said, alibaba wanted me to upload photo ID which I noped out of. Temu started spamming my email address when I’d never used them. The unsubscribe link went to their website said to adjust your account settings if you didn’t want spam… I never created and account and avoided them completely following that.
Shit, most of Amazon is that as well.
Amazon is usually OK if you buy things that are sold by Amazon or sold by the manufacturer (if it’s a well-known brand). The third-party sellers on Amazon based in China are almost always reselling stuff from Aliexpress/Alibaba with a significant markup.
Half of them aren’t in China though. It’s dropshippers, so you still get your cheap death traps, but you get them in a few days, Amazon get their enormous cut, and they get to take no responsibility when it burns your house down.
That’s why I said “sold by Amazon”. The drop shippers are all third-parties. Instead of the item saying “Sold by Amazon”, it’ll say something like “Sold by [some third party] and fulfilled by Amazon”.
Stuff sold by Amazon themselves is generally okay, since they’re directly responsible for it (no third party they can blame for any issues).
I try to avoid Amazon where possible though. B&H is pretty good for electronics, and I know I’m not going to get cheap Chinese knockoffs when I search their online store.
Seems like >70% of seller have the imprint in china or hong kong
I don’t buy anything from eBay that I can get elsewhere. I didn’t even use those other sites. Sure, everything is made in China, but I’m good not trusting China without a more reputable middleman that’s subject to American laws regarding things like refunds and such.
Isn’t that the site that’s AliExpress but worse?
Apparently for some people (my mom) the search or filters work better on Temu. No idea why, I only ever use AliExpress.
Alis search is really bad.
Somehow the auto translation is active for the product names but if you search they don’t seem to apply.
For example:
Searching for Cherry MX switches brings up articles that are named “Mechanische Kirsch Schalter für Tastatur” (essentially the name but translated). Problem is: Cherry the company is like it’s in english as well, also the fruit amd thus will not be translated correctly.
Trying to search more niche stuff quickly gets annoying when trying to find something specific.Ok, that’s fair. I just use the english terms anyways and usually also change the interface language to english.
somethings people don’t care about quality. An example, the one time I checked out Temu way back when it first made its splash I bought some targets for shooting… Hard to fuck that up and got em cheap as fuck with that promo deal they do to hook you. Uninstalled it right after, probably not worth it but I feel like that is a common experience. There are items where you just simply can’t fuck up so the ultra cheapness works out.
With that said, an obligatory FUCK temu and those like it.
Aliexpress seems most straightforward, and not quite as gimmicky.
Have you seen the wheel spin and Fomo coupons?
Maybe not as much but still highly gimmicky in comparison to normal e-commerce sitesThey don’t seem to give overall preference to a given supplier beyond their obvious coupons and paid rankings. Alibaba is better, but who needs 144 of any specific widget…?
If you compare to one of the most preferred e-commerce website, which I would consider Amazon, it’s still not that bad. I have found less lies on Ali express v Amazon. If it comes to any cheaper electronics the Ali description is the real deal as far as I have seen. Amazon I have been shipped differing products, the description or features have just been a lie, or it didn’t come with the things implied. For the most part Ali descriptions are exactly what you will expect when opening the product… in fact many times I discover extra features when receiving the product that seemingly just couldn’t explain in their marketing.
Ali>Aliexpress>Amazon… just depends on needs
My only reasons to buy on Ali is when I need something simple like velcro that can be cut to length or other small scale stuff electronics (e.g. Rasperry Pi 0) and it doesnt have to be fast.
Ironically the shipping is either free or so cheap it’s better than domestic amazon.
I often suspect they sell the same item but order it with DHL shipping (our domestic shipper) with high priority shipping included in the price (2€ item + 8€ shipping = 10€ on Amazon + “free” shipping)
A huge amount of products are just generic Chinese products that have a brand slapped on it. If you’ve ever bought a random small USB device (i.e USB hubs, etc) from a major brand like LogiTech and others, if you crack it open it is just the same device as cheap resellers with a branded coating. It’s not worth it to many companies to bother manufacturing their own small tat so they just sub-contract out.
And sure, it likely works, but it’s the exact same hardware with the same capabilities as a product a 10th of the price.
The cheap Chinese stuff often uses knock-off ICs tho.
They can be fairly difficult to detect, and will work for a short time or under very light loads. But they will be nowhere near the spec of the data sheets.
They might massively overheat, not provide the correct currents or voltages, run at lower speeds. All sorts of corners being cut to turn a $2 IC into a 50¢ IC. Or a 50¢ ic into a 5¢ oneSo yeh, might be the same PCB layout inside, it might visually look the same (or very very close) but the parts are likely to be counterfeit.
Of course, it’s also probable that name brands might be hit with counterfeit parts inside as well. Hopefully their QA picks that up
I’ve found this when trying to get a decent USB>9-pin Serial connector.
You think it’s your software, or something weird going wrong. Then you swap over a name-brand adapter, and the thing just works.
Maybe not Logitech as a whole but small scale or low-end stuff
Yeah, the small tat items and accessories, as I said.
That’s all online shopping
I can’t believe people pay full price on cheap stuff. The only reasonable thing to do is pay cheap on cheap stuff. And the delivery times are unbeatable .
I can’t believe people buy cheap trash that would be sold on Temu.
But here we are, people buy cheap ass trash off Temu. If China started picking through the trash we shipped them and sold it back to us on a site like Temu, something tells me people would still buy it.
People would buy an actual turd on temu if it’s cheap enough. Just read these comments here… But it’s cheap. Congrats, you bought cheap garbage and it got send around the globe by a company that sells your data
With how cheap they are, people will and should buy from TEMU. Aliexpress as a general store never had much of a competition for English speakers outside of Banggood for select electronics. Taoboa is good but it’s harder to use
So for you, the lowest price is the only thing that matters? It doesn’t matter whether it’s a shitty product? Or that they’re one of the least efficient shippers due to their tariff avoidance strategy, and in doing so are contributing more per purchase to climate change than even companies like Amazon and Walmart?
Dunno how it’s with Ali but doesnt Temu also use forced labor?
I’m assuming you don’t own a smartphone, because many of those materials are extracted by exploiting the local populace in Africa
I’m happy because it’s competition for Aliexpress.
Arguments against carbon emissions and carbon footprints against corporations isn’t very helpful unless you can do something about it. This is somehow a very unpopular opinion here, for some reason people don’t like being told that they don’t have much power. Boycotting it by yourself won’t work either, because even if the west gives up on it, the East will not. Carbon emissions will remain unless strict regulations are maintained, and we know who buys politicians these days. If I can do nothing about the climate, then yes I’d rather pay less. And I’m not explicitly anti-China like some people here because America is just as hypocritical.
Yes there are really bad products and their QC is horrible. I’ll say the same for Aliexpress, Taobao, Amazon, Walmart and Bestbuy. Unfortunately for everyone here, we’re going to have to choose between shit options, so yes I’d rather pay less if it’s shit I’m going to get anyway. Besides, I’m smart enough to not make bigger purchases on these sites because I know of their QC situation.
Boycotting is a collective action, it spreads like a virus, so you are wrong on its effectiveness.
You sound like someone who wants hand waive away the real costs of their actions by saying there’s nothing you can do to change things.
I hope the people who read your post aren’t demotivated to effect change because of it.
What I do not understand is why people are biased against certain companies in such a discussion. If your arguments are correct, then Amazon is a horrendous beast that should have been killed by now with “viral boycotting”. And here we are. Is anyone demotivated by knowing that people still buy from Amazon and make them billions? Why all the hate against TEMU specifically, when they’re trying to undercut Amazon and other stores? Let’s not pretend that Amazon and Best Buy and Walmart are a collective bunch of saints and can mean no harm. Where is the action in this case?
Let me speak the bitter truth for you: the majority of the population here is American, with an inherent anti-chinese mentality when it comes to capitalistic ventures/operations. That is the reason for the hate. Alibaba faced the same issues, and in case someone wants to bring up Huawei for their actions, remember that AT&T runs an NSA spy-mission in Manhattan. Where is the outcry in this case?
I might have veered off-topic, but bad QC and cheap deals aren’t inherently a Chinese thing. Hence, I do not follow the propaganda against Chinese shops who are beating American companies at their own game.
Edit: since I’ve been called guilty of waiving away untoward actions, please enlighten me on how the general American population has stayed “responsible” and managed to put any dent in other non-Chinese companies that have their ethics in the dumpster and actively harm the environment and people (I’m looking at you Nestle, Spotify and OpenAI)
I can’t force people to do the things I think they should. Noone can. People draw inspiration from all sorts of things. Like you right now seem inspired to protect China from racist western policies.
I dont pretend to speak for my country, or its government, but I can do two things:
-
Walk the walk, if you believe something then follow it. Examples: de-googling, disengaging with social media, following a vegan lifestyle, research companies before giving them your money.
-
Talking about all of this stuff in public places. With my family, coworkers, or here on Lemmy, anything we say has the potential to inspire someone to change. You never know what will be the thing that triggers change, but for all the things I listed above I had someone share that information with me in a public forum, which caused me to change.
I’m sure we can argue the efficacy of this strategy all day, and even some of the examples you gave like Amazon are no longer the behemoth they used to be.
After coming back from a break, I realised I might have leaned too hard into “protecting Chinese companies”. I will say this right now for everyone reading: I have no love for the nationality of said companies. I don’t care if Aliexpress or a clone of theirs was Chinese, Korean, Brazilian, Swiss, Russian, Iranian, Australian or Japanese (incidentally I spend time on buyee.jp because the cheap deals on CDs sometimes). What I care about is providing competition to the bigger mammoths here. If I find a USB adapter for a quarter of the price with free shipping and refunds from a Chinese shop with a decent reputation (Aliexpress, Banggood, TaoBao and now TEMU), I’ll take it. I hope this forces big American retailers to maybe give better, fairer prices to their customers.
I’m not quite convinced that Amazon is no longer the giant with worms as we knew it. Can you explain?
-
I’m anticonsumption in general and temu just seems like the epitome of paying for disposable garbage.
In general i don’t understand why people are buying any nonessential items at all. Everyone is apparently too poor but random crap still sells. I splurged and bought a cheap tablet to use as an ereader this year but only because i can’t justify the expense of buying books and my local library is awful.
Well, at least you’re consistent with your views. Being anti-consumption is a fine stand. In my case, I usually go to these sites for cheap deals on microcontrollers, tit-bits like USB adapters, metal stands, IEM cables etc. I’m not buying expensive/essential stuff from them.
Yes there are really bad products and their QC is horrible. I’ll say the same for Aliexpress, Taobao, Amazon, Walmart and Bestbuy.
There’s a huge difference between some 5/10 products at Walmart and Best Buy and the best case being a 5/10 product with the majority being 2/10 and some being actually dangerous like Temu.
They’re not remotely similar.
Depends on what you buy. You shouldn’t be buying PSUs or TVs or something of the sort from there, but try finding cheap clothes, accessories, electronics like that on Amazon
You shouldn’t be buying anything from there.
Those cheap clothes would be overpriced at free.
And where am I getting such cheap clothes if I don’t have a thrift store near me? I’d happily take them for free.
And clothes are just one part of it, which I don’t really purchase that often (I mentioned them because I bought a few boxers to wear around the house but that’s it)
The irony
First, you use Lemmy, that’s great. But pls use a client without ads…
Been using Boost since it was a Reddit client. By default, it is my go to.
Maybe but you’ve done the transition to Lemmy try to use a libre client
I’m all for Libre but in this case @rmayayo@lemmyworld is my leader.
Who is he?
He is the dev who made Boost.
Why does he done it with ads?
100% this. Boost is great
by “client” do you mean “just use a browser”?
Or, you know, the 98% of clients that don’t have ads. I, for one, recommend Voyager.
Maybe but not only, for phone I recommend an app that’s much more optimized for using on mobile
Lemmy website is fine on mobile imo. Not perfect but usable and optimized.
For sure! Personally I prefer using the app
You can pay just a few dollars to remove the ads from Boost.
Bro why using Lemmy if it’s for using proprietary client? Voyager, Jerboa, you have others choice…
Ask the 100,000 people that downloaded Boost, not me.
Probably people who have been using Boost for Reddit before and now want the same experience but for Lemmy
But with this change from reddit to Lemmy the should have done the same thing for their client
Where are you viewing Lemmy posts that you have ads?
I’m using Voyager and it’s great. I don’t even use the app, I prefer the PWA.
I also use Voyager and agree, plus it’s actually open source.
I think it’s the Boost app.
I see; I can’t imagine willingly submitting to ads, but whatever works for them.
Yeah. Boost itself is great though. Well worth the couple of bucks to get rid of the ads forever.
What does Boost have over clients like Voyager?
Ads
Ads for a platform with political views that despise them. Ironic
I use it too. Tried a few different ones and like boost the best. I finally just paid for the non-ad tier. One time cost of 3.99. I would have been turned off by a subscription.
Yeah boost is definitely good, it was my main app until a few months ago. Recently I have been trying Connect, which is another great app.
Connect has improved a lot since I first tried it, also doesn’t have any ads. But all things considered - Boost is bit more polished than connect.
What’s wrong with voyager? Its already ad-free.
Seems so strange to choose to inject adds over top of lemmy by choice.
And it has come a long way too. In fact, I just donated since it’s struck me how solid of an experience it’s been.
That’s what you get for using a proprietary Lemmy app. Switch to Thunder, it doesn’t have ads, it’s open source and in my opinion has the best UI out of all Lemmy apps. Also support the development and join their community: !thunder_app@lemmy.world
From the screenshots alone the interface looks similar to sync
Jerboa here but same
I tried using Jerboa and found it to be incredibly buggy and poorly designed. Not sure what’s going on there, considering that it’s the official mobile app made by the Lemmy devs
Has worked mostly fine for me, YMMV
Do you think it’s better than Voyager? That’s what I’ve been using. Pretty satisfied with it.
Snap! Double irony
Lol
I generally think arstechnica.com does a decent job of being a non-garbage news site. I pay a couple bucks a month for the ad-free RSS feed. This story feels terrible to me. I don’t doubt a law suit has been filed, but I would expect some investigation by the reporter of the extra-ordinary claims of privilege escape the application is claimed to be capable of.
Given that the headline says that it is a claim in a lawsuit, and the lawsuit is by a state attorney general and not some random nobody, I feel like they are being fairly reasonable.
Yes because AG’s from repub states never ever file frivolous lawsuits that suit their own agenda.
I would feel that it would be a reasonable if it was my local paper running the story. Arstechnica IS a primarily technical news site—I believe they should have a higher bar—otherwise they are just parroting a report and not providing useful (to me) news.
Shocked i tell you. I am shocked.
No way an app would collect data it doesnt need. Preposterous.
Next thing you’ll tell me is that tiktok is doing the same thing!
What about Meta and Google?
it doesn’t count when it’s an american company doing it
Them too, but lukewarm by comparison.
Erm, WhatsApp would suggest otherwise.
WhatsApp was the vector for zero click access to a target’s phone from Israel’s weapons grade hacking Pegasus toolkit. They would send a video call, typically in the middle of the night, and with no input from the used they’d get full access. My personal belief is that they used functionality WhatsApp itself uses to access user data.
There was also an encrypted phone called ANOM, which had this trick calculator app with a hidden encrypted messager. “Made for criminals, by criminals”. Except, when the guy started his business he got investment from the FBI and Australian Federal Police to pay for the servers and some of the phones themselves. Basically every time it sent an encrypted message it sent a separate encrypted message to the ANOM servers. It’s entirely possible (perhaps even likely) that WhatsApp would do this also.
As for Google, they’re truly insidious. Lots of banks now require you to connect to Google captcha servers - they don’t give you the pictures, it’s just the back end, basically the tracking parts. Then there’s the controversy about them collecting location data when users have said no. They absolutely do collect data they shouldn’t.
I’ll accept that maybe I’m giving Google a pass because of misplaced nostalgia, and while I personally have never used or liked
MetaFacebook, I’ll concede that for a while it provided a service some people valued.It’s still my opinion that Google and Facebook have a large percentage of engineers that personally try to make them a genuinely good service, at least moreso than compared to TikTok and Temu. But I’m willing to concede it’s not as much a practical difference as I would like.
It’s still my opinion that Google and Facebook have a large percentage of engineers that personally try to make them a genuinely good service
Most of those people were sacked long ago. Today’s menu for those that remained is shareholder maximum value extraction sausage fest
Why do you say that?
Cause they are owned by American billionaires and as such are more ethical. /s
Like Tim Apple, iPodJockey?
I was given this nickname by an old guy at work that knew I was good with computers. Never actually owned an ipod lol.
Emphasis on by comparison, as in “molten hot metal is cooler than the surface of the sun, by comparison”.
TikTok and Temu actively have code in them that would be considered a virus in other contexts. They exploit your system to gain more access than they should, violating the point of sandboxed access.
By comparison Meta and Google merely take advantage of user ignorance and apathy by making opting out frustrating - but still technically doable.
Both practices are terrible, but that’s not the same as saying they’re equally bad.
By comparison Meta and Google merely take advantage of user ignorance and apathy by making opting out frustrating - but still technically doable.
This is simply just not true. Meta used an adversary-in-the-middle attack to decrypt Snapchat and other competitors traffic. Facebook, Apple, Twitter and Google have been intercepting traffic since before https/sandbox/anti-virus were the norm. Do you think they didn’t do anything malicious?
Install any Google app on Windows and it will install a task schedule and a always online background service to “check for updates” and downloads and runs their executable without any user consent. I wonder why no body had a problem with that. hmm…
Google runs it own operating system so they could technically do anything they so fucking please. You think Chinese Android variants are using exploits or just scooping data wholesale, because it can. But you think Google and Apple aren’t?
It’s showing your prejudice, bias and concern trolling more than anything.
Have any of you actually ever stopped to process what the tagline, “I’m shopping like a billionaire” means?
I’ve always interpreted it as,
I’m needlessly buying things that don’t make me happy, but making the purchase without any hesitation, knowing that the purchase price could never financially impact me in any real way. When I purchase the thing, I’ll probably never use it or actually take it out of the box even. It is just empty, hollow. And somewhere inside, I always know that it’s all only possible, because I’m actively exploiting the cheap labor of scores of other people that are made to perpetually suffer in generations of abject poverty to allow for my relative comfort…
🎶*“I’m shopping like a billionaire!”*🎶
I am disabled and have limited income I don’t have control over increasing or decreasing. I use temu to save a lot of money on essential things that should be cheap but are still overpriced in America. Sponges. Rags. Soaps. Pens. Tools. Home improvement hardware. Plant grow supplies. Gifts for me nieces. The tagline, is just a tagline. Billionaires are not like me and scouring for cheap magic sponges.
Edit: also, temu did not invent drop shipping. Shopping on amazon is literally the same thing.
Good to know people that are disabled don’t mind using shitty maleware apps, I guess?
What’s your point combining using the malware app with you being disabled? Is that supposed to make the app better somehow?
You’re not special because you’re disabled. Things you use aren’t magical amazing. You’re still the same as everyone else.
That’s… not what they were saying? They were responding to a comment saying it encourages consumerism by saying that they use it for better prices on things they need regardless
What does being disabled have to do it?
That’s why they’re broke
Well this disabled person thinks you’re a dumb asshole.
For what reason exactly?
Other commenters have already corrected your thinking, don’t pretend like you didn’t read them.
I completely forgot about this post. I’m not going to read any more comments than I did however long ago the conversation originally was. Oh shit it’s almost 2 weeks old lmao I don’t give a fuck
My interpretation of that tagline is that since the prices on Temu are cheap, it means you can shop as if you had a lot of money, without actually spending that much.
I think you cracked the case on that one, that’s gotta be what it means.
All I want to know is what do these Temu people think my life is like?

Are you a busty outdoorswoman?
Weaponized fishing for covert military operations.
On a skateboard… with tits!
Code Name: Go Fish!
I mean, you’re obviously a sexy military mechanic woman, who goes into battle with fantasy battle armor and goes fishing as a hobby! Duh.
The bearings combined with the wrenches made me think, like, roboticist. So maybe they make fishing robots that double as sexbots?
Trust me, fish dont need to be robots to be fucked…
Any good RPG has a solid fishing mini game tbh
I was wondering what that blue thing was. I thought it was a weird personal tool…
It looks like an archery release, used by compound bow shooters to pull the bow string back and release with a trigger or button
Clearly you use adbloker or something cause temu just got excited when you opened up the link.

It just thinks you’re a garden variety redneck.
Your life looks pretty sick to me!
he’s batman
Batwoman
No, you don’t get it.
These massive Batman pecs need support.
Batmare
Bustybats
deleted by creator
Yesterday, I saw a Temu ad for something and I just wanted to open it to read the info and there were so many popups and “spin the wheel for a prize” and “enter your email here” and so on that I gave up and just looked for the info elsewhere. Never clicking on a Temu link again.
I get their CAPTCHA where I have to slide the puzzle piece over to look at one of their ads. More than half the time I will do this and it will fail saying I didn’t do it right. So yeah temu has become a trash site.
"So yeah temu has become a trash site. "

That CAPTCHA isn’t specific to Temu.
one of the best decisions you’ll ever make, next to dns level blocking it on your network.
I’m shocked, I say. Shocked!
The idea of an app being used to gather additional datea from a customer!“Additional date”
Comments here: “Yeah right, I’ll believe it when they explain how.”
Article: literally has a section explaining how
Edit:
Replies: “Yeah, but that’s just a summary. I’ll believe it when they explain in full detail.”
Article: literally has a link to the detailed explanation
The claim is they completely bypass all Android and iOS security is pretty unbelievable.
If so then the real discussion is how these zero day exploits are just sitting around.
EDIT: It seems the focus is on Android but all the information is nonsensical, like AI generated buzzword bingo.
That source looks better indeed.
Ars quotes nonsense like “bypasses the security” and “exploit the user”.
Those terms have meaning and they aren’t applicable here.
At the end though they do say things like
is able to hack your phone from the moment you install the app
Without any credible evidence.
It states that it’s somehow breaking the permissions sandbox by dynamically recompiling code after the app is opened. Unless there is some undisclosed exploit that it’s using to break the sandbox, it’s outside most people’s understanding of how these platforms work
It only explains how it would pass (automatic) reviews. Not how it would bypass the sandbox. So yeah, you’re right, not enough info sadly.
Someone else posted this report in this thread which does a good job of the deceptive practices and API calls the app uses to trick the user into giving permissions up willingly and otherwise collect data it shouldn’t.
Like a worse AliExpress
Also fuck their landfillware Chinesium “products”.
That’s also most of what’s on Amazon these days.
Amazon is just faster shipped temu garbage
Every person I’ve heard hate on temu shops on amazon, too. It’s pretty ironic.
If it’s $5 and some random assortments of letters for a brand name you might as well just light your money on fire whether you order from temu or amazon or Walmart for that matter
I mean, some things are just fine when they are the cheapest?































